This looks really bad forensic reporting from this point. Where was the mess up? examiners? prosecution?
Casey Anthony Likely Googled 'Foolproof Suffocation': Report - HuffingtonPost
g33ks3cUr - Security Stuff
Sunday, November 25, 2012
Wednesday, November 14, 2012
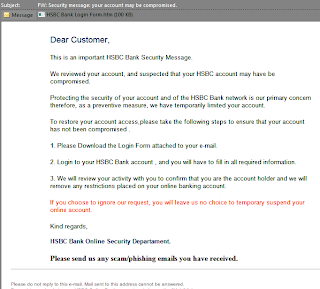
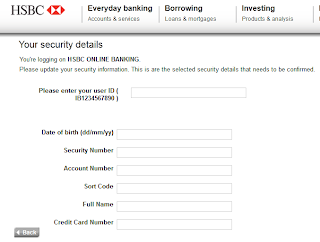
HTML attach phishing
Nothing groundbreaking, just another sneaky little phishing trick via an html file attached to an email.
Going through the file manually shows a lot of valid HSBC links/images for presentation to the user. However look at this little "post" fella...
Here is the finished product:
Looks legit right?
Saturday, June 2, 2012
Obama Order Sped Up Wave of Cyberattacks Against Iran - New York Times
Nothing new or groundbreaking in this article, but it does a nice job of bringing together some of the pieces and there is a nice "How a Secret Cyberwar Program Worked" graphic.
"WASHINGTON — From his first months in office, President Obama secretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s main nuclear enrichment facilities, significantly expanding America’s first sustained use of cyberweapons, according to participants in the program."
Story link > here <
Thursday, April 5, 2012
Mac OS XJava Flaw
According to Dr.Web more than 55,000 Macs are infected with the so-called Flashback Trojan. The vulnerability that the attackers are using is with the Java for OS X Lion. (CVE-2012-0507)
My .02: With the popularity of Apple products going up and up, it was only a matter of time that attacks started shifting (even ever so slightly). While MS boxes have been and will be targets for a long time, the Mac world has been slowly becoming into focus for attackers. However, I'd suspect there to be a bigger attacker push into the mobile platforms rather than Mac in the coming year(s). Mobile platforms (iOS & Android) are more ubiquitous by far and more people would have a cell phone than a computer of any sort. Besides, people do stuff on their phones they would never do on their computer...the weak link gets weaker...
More reading:
Ars Technica - Mac Flashback trojan exploits unpatched Java vulnerability, no password needed
Krebs on Security - Urgent Fix for Zero-Day Mac Java Flaw
My .02: With the popularity of Apple products going up and up, it was only a matter of time that attacks started shifting (even ever so slightly). While MS boxes have been and will be targets for a long time, the Mac world has been slowly becoming into focus for attackers. However, I'd suspect there to be a bigger attacker push into the mobile platforms rather than Mac in the coming year(s). Mobile platforms (iOS & Android) are more ubiquitous by far and more people would have a cell phone than a computer of any sort. Besides, people do stuff on their phones they would never do on their computer...the weak link gets weaker...
More reading:
Ars Technica - Mac Flashback trojan exploits unpatched Java vulnerability, no password needed
Krebs on Security - Urgent Fix for Zero-Day Mac Java Flaw
Sunday, March 25, 2012
Incident Response Essentials p2
We left off at listing some of the bare minimum of artifacts needed to conduct analysis on systems that are suspected of being compromised. Before we get to tools there should be some discussion about "how" to get the artifacts.
The focus will be the acquisition of these artifacts on live systems. There are big differences in live and dead host acquisition, but right now I am focusing on live remote acquisition on an enterprise level.
So what do you need to do live remote acquisitions?
Network access:
Goes without saying, but if your enterpise has firewalls/host ips agents/ipsec/networking filtering/DACLs protecting hosts you will want to get some sort of pre-planned access capability. If you don't you will waste valuable time getting what you need... A little pre-planning here is key. Since we are talking about a Windows environment you will typically see systems with Windows SMB (a.k.a File & Printer Sharing) access. (IPC$).
Authentication:
In short, you'll need to be authenticated as a user with administrator privileges. Whether this is a domain admin account in the local admins group or local account, you need to have admin privileges to snag these artifacts. You'll also need that level access to connect to the box remotely.
Protecting Privileged Domain Accounts: Safeguarding Password Hashes
So you have access and the rights. Now what?
At this point you've identified the target system, you have access, now you need to get the tools/scripts to the box. **depending on your tool(s). Some tools don't have remote capability so getting them on the target box is needed.
You can do this by manually mapping and copying, copying the files from a central repository, or even have them pre-deployed on the box. (I am not necessarily a fan of pre-deployment...considering your pre-deployed tools could be tampered with on the compromised system). Utilizing a central repository can give you control over the files but allowing the ability to pull the files down to the suspect system.
To actually run the tools you will need the ability to run commands remotely. To stay with the enterprise Windows environment, PsExec is an excellent tool for these type of operations. (do it securely though, depending on how you do it, it can pass the password in cleartext.) Consider launching a command prompt on the local system with the IR account, and then run PsExec. The remote process will run under the account PsExec was launched from, and in this case it will be the IR account.
The focus will be the acquisition of these artifacts on live systems. There are big differences in live and dead host acquisition, but right now I am focusing on live remote acquisition on an enterprise level.
So what do you need to do live remote acquisitions?
Network access:
Goes without saying, but if your enterpise has firewalls/host ips agents/ipsec/networking filtering/DACLs protecting hosts you will want to get some sort of pre-planned access capability. If you don't you will waste valuable time getting what you need... A little pre-planning here is key. Since we are talking about a Windows environment you will typically see systems with Windows SMB (a.k.a File & Printer Sharing) access. (IPC$).
Authentication:
In short, you'll need to be authenticated as a user with administrator privileges. Whether this is a domain admin account in the local admins group or local account, you need to have admin privileges to snag these artifacts. You'll also need that level access to connect to the box remotely.
- Side note: You are likely responding to compromised systems with elevated privileges across the organization, and when investigating these systems those credentials could become compromised themselves. You need to adjust accordingly and I suggest creating a privileged account that is only used for IR work and heavily defended: quickly expiring passwords, heavy logging alerts on it's use, etc...
Protecting Privileged Domain Accounts: Safeguarding Password Hashes
So you have access and the rights. Now what?
At this point you've identified the target system, you have access, now you need to get the tools/scripts to the box. **depending on your tool(s). Some tools don't have remote capability so getting them on the target box is needed.
You can do this by manually mapping and copying, copying the files from a central repository, or even have them pre-deployed on the box. (I am not necessarily a fan of pre-deployment...considering your pre-deployed tools could be tampered with on the compromised system). Utilizing a central repository can give you control over the files but allowing the ability to pull the files down to the suspect system.
To actually run the tools you will need the ability to run commands remotely. To stay with the enterprise Windows environment, PsExec is an excellent tool for these type of operations. (do it securely though, depending on how you do it, it can pass the password in cleartext.) Consider launching a command prompt on the local system with the IR account, and then run PsExec. The remote process will run under the account PsExec was launched from, and in this case it will be the IR account.
Wednesday, March 14, 2012
Incident Response Essentials p1
Obviously there are multiple layers and scenarios to consider when responding to incidents. And the tools you use to detect/collect/analyze/mitigate really depend on the threat scenario.
So what are the basics? What do I need for the bare minimum for response operations? (w/ a focus on Windows systems)
Below is a list of the items I like to collect for response operations: (your mileage may vary)
- $MFT- Master File Table for later parsing/analysis
- Prefetch files
- ntuser.dat(s) - just grab em all...
- AutoRuns - reg entries/startup folders/services/etc.
- Network info - ipconfig/netstat - dnscache - hosts file
- Event Logs - OS logs - AV logs - other app logs (if applicable)
- Scheduled Tasks
- Loaded DLLs
- Memory Dumps** If possible I like to capture the running memory from the system if space and time allows. A lot of good stuff can be pulled out of running memory if you want to learn about the malware/attack more. Will go deeper into this topic in a later post.
BTW, you can get this information easily utilizing some scripting and free tools. I'll cover those tools (free & not free) in another blog post.
Tuesday, November 1, 2011
FBI says Russian spies got close to Cabinet - Washington Times
Some interesting tid bits about the Russion spy ring break up last year:
[snip]-- a key break in the case developed in the mid-2000s after the FBI was able to decipher coded electronic communications between Moscow and the deep-cover spies. The communications were used to unravel the network, ending the FBI probe that began more than a decade ago.
Breaking the electronic codes used by the “illegals,” as the Moscow spies are called, was a milestone in the case that allowed FBI agents to pose as the spies’ handlers and identify the spies.
“Ultimately, at the end of the case, we were able to become the Russians,” Mr. Figliuzzi said. “The point where we decrypted the communications allows us to basically own the network.”
Full story at the Washington Times: FBI says Russian spies got close to Cabinet - Washington Times
Subscribe to:
Posts (Atom)